Apr 29, 2025
How Strong Audit Trails Power FinTech Compliance: Importance & Purpose

By Fraxtional LLC

For FinTech founders, executives, and risk leaders, an audit trail isn't just a technical requirement; it's a critical component of your compliance success. In a fast-evolving regulatory scene, an audit trail serves as a foundation for accountability and trust.
Regulators, banks, and investors scrutinize your audit trail not just to verify compliance, but to understand how effectively you manage risk and maintain control. Missing or incomplete audit trails can raise red flags, triggering more intense scrutiny and slowing down your growth.
That's where fractional leadership steps in. A fractional compliance officer brings the expertise needed to ensure your audit trail is not only solid but also defensible under regulatory scrutiny.
This guide will walk you through what an audit trail is, why it's vital to your compliance program, and how strong leadership can turn your audit trail into a strategic advantage rather than a liability.
Key Takeaways
- Audit trails are evidence, not metadata. If actions can't be reconstructed with context, approvals, and timing, controls can't be defended.
- Logs ≠ audit trails. Raw system logs without attribution, rationale, and sequencing don't meet the expectations of regulators, banks, or investors.
- Overrides without explanation are treated as control breakdowns. Unapproved or undocumented exceptions are one of the fastest ways audits escalate.
- Stakeholders read audit trails differently. Regulators test control execution, banks assess partner risk, and investors judge governance maturity, all from the same trail.
- Leadership turns audit trails into trust. Vigorous systems capture activity; accountable oversight makes that activity credible under scrutiny.
What Exactly Is an Audit Trail?

An audit trail is a tamper-resistant record that lets an independent reviewer reconstruct events: who did what, when they did it, what changed, and how it was approved.
This isn't abstract. U.S. financial regulation explicitly bakes auditability into recordkeeping. For AML/BSA compliance, the FFIEC's BSA record-retention appendix states that most BSA records must be retained for at least 5 years.
These timelines set the baseline for how long your audit trail must remain usable, searchable, and defensible.
A strong audit trail captures the minimum facts a regulator, bank, or auditor needs to verify accountability:
- User attribution: the person or system identity behind each action
- Timestamps: time-ordered steps (create, review, approve, override)
- Change details: what changed, not just that “something happened.”
- Approval path: who reviewed it, and under what authority
- Integrity controls: evidence that the record can't be silently edited or backfilled
Audit standards explicitly require auditors to obtain sufficient appropriate audit evidence. If the trail can't support the assertion being tested, it doesn't count as strong evidence.
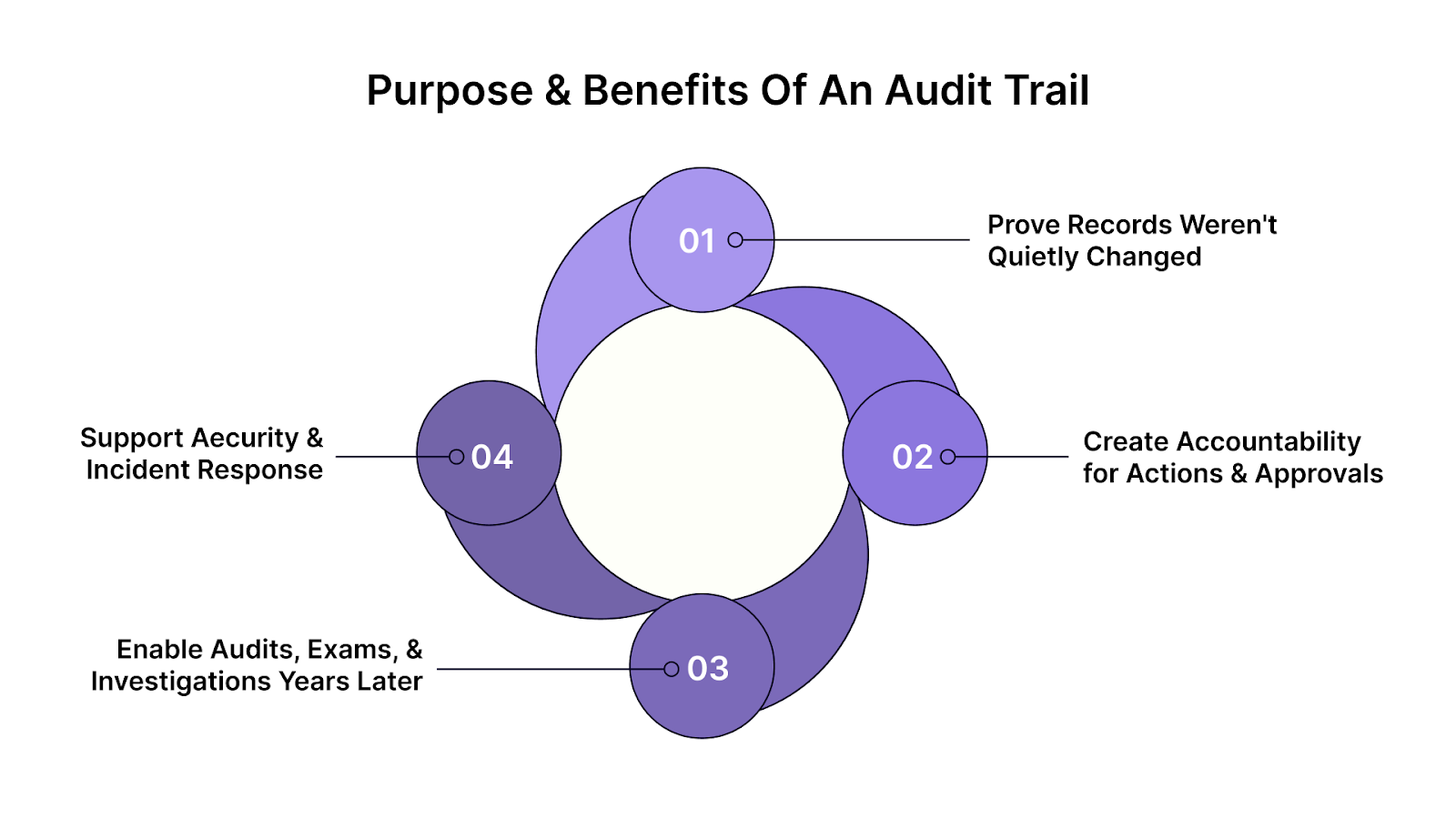
What Is the Purpose and What Are the Benefits of an Audit Trail?
An audit trail exists for one reason: to make your compliance story provable. Key benefits of a strong audit trail include:
- Enhanced Trust: A robust audit trail signals transparency and accountability, earning the trust of regulators, banks, and investors.
- Regulatory Readiness: Being prepared for long lookbacks and scrutiny helps avoid last-minute scrambling during audits.
- Risk Mitigation: With clearly documented decisions, you reduce the likelihood of compliance failures or breaches.
- Security Assurance: Helps identify and resolve incidents quickly, ensuring you can respond effectively to compliance and security issues.
Benefits of Maintaining an Effective Audit Trail
In a FinTech audit, it's not enough to say "we have controls." Regulators and banks want to reconstruct what happened and verify that decisions were authorized, time-bound, and reviewable.
Here's what an audit trail is designed to actually do, in practical terms.
Alt text: What Is the Purpose and What Are the Benefits of an Audit Trail?
1) Prove Records Weren't Quietly Changed
Audit trails protect integrity. If a record is edited or deleted, reviewers want proof they can re-create the original and see every change.
That expectation is explicit in U.S. securities recordkeeping. FINRA's Rule 17a-4 amendments explain that firms can meet preservation requirements either via WORM storage or an electronic system that maintains a complete, time-stamped audit trail of modifications and deletions.
2) Create Accountability for Actions & Approvals
Audit trails tie actions to people and approvals. That's the difference between “a setting changed" and "a designated reviewer approved the change.”
This is also spelled out in the regulated electronic record rules. For example, 21 CFR Part 11 requires secure, computer-generated, time-stamped audit trails that record actions that create, modify, or delete records. It explicitly states that changes must not obscure previously recorded information.
3) Enable Audits, Exams, & Investigations Years Later
Audit trails are built for long lookbacks. Regulators often review activity far beyond the last quarter. Many BSA/AML-related records must be retained for at least 5 years (FFIEC BSA retention guidance).
If your audit trail can't support those timeframes (or can't be searched and reproduced), it becomes a compliance risk even if today's controls look fine.
4) Support Security and Incident Response
Audit trails also protect you when something goes wrong.
NIST guidance on log/audit trail management highlights that audit records help identify potential security violations, support investigations, and aid in reconstructing what happened after incidents.
For regulated FinTechs, this matters because fraud, AML, and cybersecurity events often trigger the same question: show the sequence, the approver, and the response time.
At Fraxtional, we specialize in providing independent audit services that ensure your audit trails are not only complete but defensible. Our experts help you build a transparent audit-trail framework that meets regulatory expectations and minimizes risk. Contact us today!
What Are the Primary Types of Audit Trails
Audit trails can be categorized by the areas they monitor and the level of detail they capture. Each type of audit trail serves a specific purpose and is crucial for maintaining regulatory compliance, ensuring operational transparency, and enhancing security.
Here are some key types:
1. Transaction Audit Trails
Used in industries like finance and retail, these track details of financial transactions, who made them, when, and what they involved. For example, brokerage firms use transaction audit trails to track trades and prevent market manipulation.
2. User Activity Audit Trails
Common in IT and security, these trails log user actions within systems, such as logins, data changes, and system accesses. This is critical for ensuring data security and preventing unauthorized access to sensitive information.
3. Compliance Audit Trails
Required in industries such as healthcare and finance, these trails focus on actions related to regulatory compliance. For instance, healthcare providers use audit trails to track access to medical records and ensure compliance with HIPAA regulations.
4. System Audit Trails
Used in IT infrastructure, these trails monitor system-level events, including server logs, network traffic, and security incidents. They help detect potential security breaches or malfunctions within critical systems.
5. Operational Audit Trails
These are used across businesses to track workflow and operational processes. They help identify inefficiencies or potential fraud in operations by logging each step of a process from start to finish.
Each type of audit trail ensures accountability and transparency, serving as a key tool for risk management and regulatory adherence across various sectors.
Also Read: Effective Audit Risk Assessment for Financial Firms
Why Audit Trails Fail in FinTech & Regulated Teams

Audit trails don't fail because teams lack data. They fail because the record can't survive scrutiny: you can't reconstruct decisions, prove integrity, or meet retention expectations.
Logs often capture events without the elements auditors need: who approved, what changed, and why, which forces auditors to rely on human explanations, thereby expanding testing and increasing risk.
Additionally, as teams grow, shared accounts, vendor actions, and permission sprawl make it hard to prove individual accountability. Overrides are normal in real operations. The audit problem is overridden without:
- documented rationale
- named approver
- time-stamped escalation path
That's a control integrity problem.
If your audit trails also rely on explanations instead of evidence, Fraxtional can help you identify where accountability breaks before auditors do. Review your current audit trail structure with leaders who know which gaps regulators escalate first. Reach out to us to start the conversation.
Audit Trail Requirements Regulators Actually Care About
Most "audit trail" advice online is just logging guidance with a new label. Regulators and sponsor banks are tighter than that. They look for evidence that survives a lookback, a challenge, and a reconstruction.
Here's the minimum viable audit trail standard that holds up in FinTech compliance, using the same attributes regulators hard-code into recordkeeping rules.
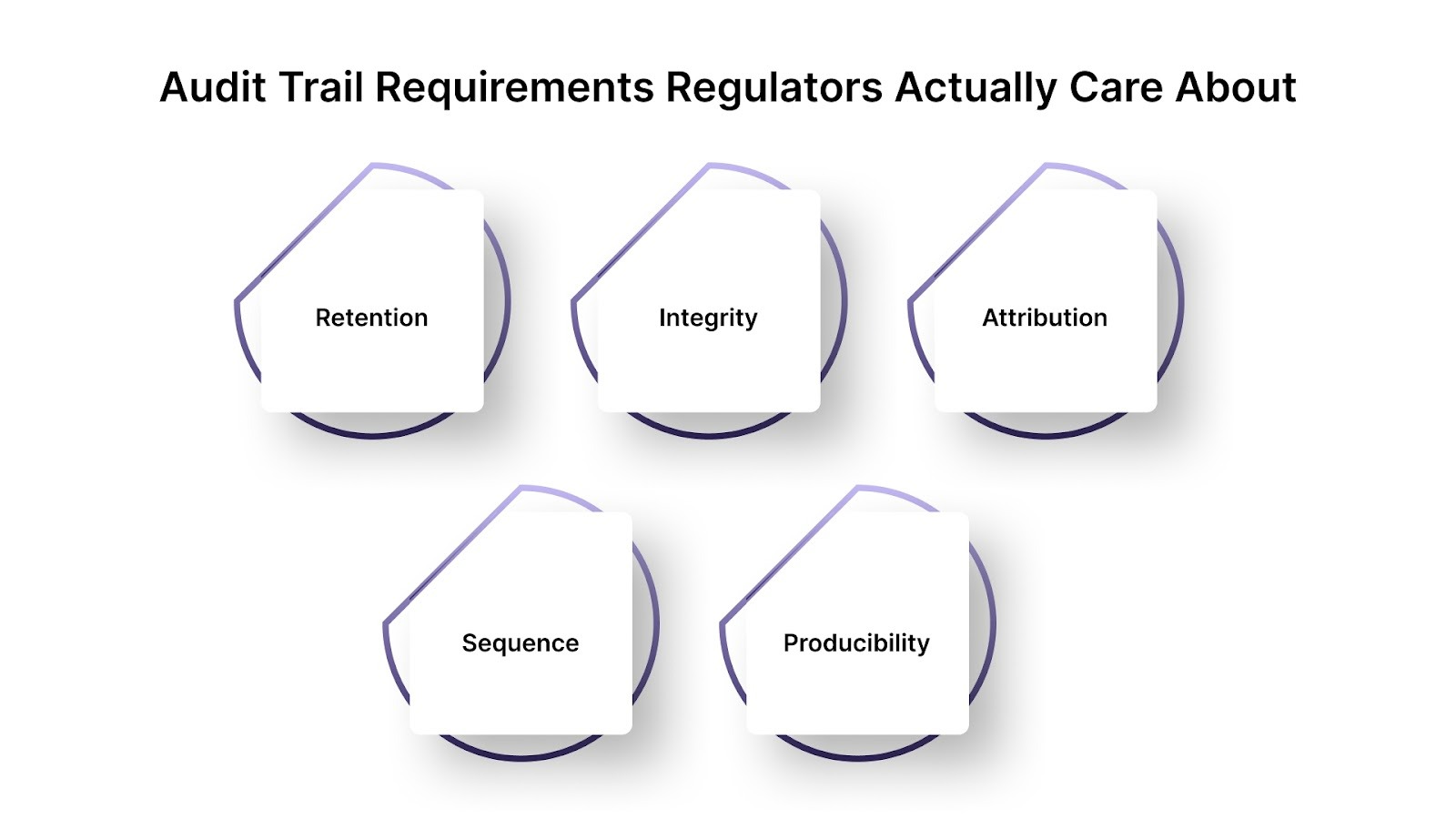
1. Retention
If your audit trail can't live as long as the rule requires, it's not an audit trail. It's temporary telemetry.
FFIEC notes that most BSA records must be retained for at least 5 years. Additionally, banks must retain certain CIP information for 5 years (see 31 CFR 1020.220).
2. Integrity
This is the difference between "we have data" and "the data is admissible."
The SEC's 2022 amendments to Rule 17a-4 explicitly introduced an audit-trail alternative to WORM preservation, reinforcing the regulators' preference for a system that proves records weren't silently altered.
3. Attribution
"User123 changed it" isn't enough when permissions change monthly. A defensible audit trail shows:
- Who initiated the action
- Who approved it
- What role/authority they had at that time
- Whether a vendor or service account touched it
4. Sequence
Audits are time-based. If you can't reconstruct the order of events, you can't prove controls operated. This is why recordkeeping regimes lean on chronological, time-stamped capture.
5. Producibility
An audit trail that exists but can't be queried, exported, or explained becomes an audit delay. NIST's log management guidance is blunt: records must be stored in sufficient detail for an appropriate period, and usable for auditing and investigations.
Knowing the rules doesn't guarantee compliance. The real risk shows up in how those requirements break down in practice. Let's see that ahead.
Also Read: How Substantive Testing Ensures Accurate Financial Audits
Common Audit Trail Gaps That Trigger Findings

Audit trail findings usually happen when reviewers can't do one thing: replay the story without you in the room. Below are the gaps that trigger expanded testing in FinTech audits, plus practical fixes that align with what regulators actually require.
1) Retention is shorter than the regulatory lookback
What auditors see: logs roll off after 30–180 days, or trails become inaccessible after a migration.
Why it triggers findings: BSA/AML frameworks commonly require at least 5 years retention for many records, and SEC/FINRA broker-dealer regimes include 6-year preservation requirements with accessibility expectations.
If the trail can't survive the lookback, it fails regardless of how clean the current period looks.
Fix this gap:
- Set retention to the strictest rule that applies to your product and licensing footprint
- Keep trails searchable and exportable after system changes
- Document retention logic so it’s defensible in audits
2) No proof records weren't edited or backfilled
What auditors see: a record exists, but there's no verifiable history of edits, deletions, or approvals.
Why it triggers findings: SEC recordkeeping updates explicitly recognize an audit-trail alternative to WORM preservation, reinforcing the expectation that reviewers will require you to prove integrity, not just storage.
Fix this gap:
- Ensure edits/deletions are logged with before/after values
- Restrict write permissions and log every privileged action
- Make audit trails immutable or cryptographically verifiable where appropriate
3) User attribution breaks (shared accounts, vendor actions, role drift)
What auditors see: "system" or a shared account executing actions, approvals unclear, roles changed, and authority can't be confirmed.
Why it triggers findings: In regulated reviews, attribution is accountability. If you can’t tie the action and approval to the proper authority at the time, the trail can’t support audit evidence standards.
Fix this gap:
- Eliminate shared accounts for approvals and exceptions
- Require named approvers for high-risk changes and overrides
- Preserve role/permission snapshots (who had what access at the time)
4) Trails are “machine readable” but not “audit readable.”
What auditors see: raw logs without a transparent chain of events, forcing manual reconstruction.
Why it triggers findings: NIST emphasizes that logs must be stored with sufficient detail and be usable for audits and investigations. If auditors can’t query and reconstruct quickly, audits expand, and timelines slip.
Fix this gap:
- Create standardized event schemas for key controls (who/what/when/why)
- Build simple exports that show full sequences (initiate → review → approve → execute)
- Maintain a data dictionary so terms and fields are consistent
5) Audit trails aren't tied to controls or policies
What auditors see: events exist, but they can't be mapped to a control, risk decision, or policy requirement.
Why it triggers findings: Audit evidence standards require that evidence support the conclusion being tested. If you can’t link trails to controls, you can’t prove the control operated.
Fix this gap:
- Map trail events to control IDs and policy sections
- Define which events constitute “control performed’’
- Keep evidence packages consistent across audit periods
These gaps rarely stem from tooling alone. They usually reflect missing ownership and governance over how audit trails are designed, maintained, and reviewed. Addressing them requires clear leadership oversight, not just technical fixes.
Leadership Oversight in Audit Trail Design and Management
Leadership is the foundation of a strong audit trail system. While technology captures data, leadership oversight ensures that audit trails align with compliance goals, business operations, and risk management.
- Leaders must define the structures for user attribution, timestamps, and approvals, ensuring that every action is traceable and defensible.
- Effective leaders don't just implement systems; they nurture a culture of accountability, ensuring that every change is documented with a clear rationale and approval.
- They also establish regular reviews and ongoing monitoring to identify gaps before they turn into risks.
In doing so, they ensure that audit trails remain a trusted asset, strengthening compliance and building confidence with regulators, investors, and partners.
If you're planning system changes, vendor migrations, or remediation work, Fraxtional can help ensure audit trails remain intact through the transition. Fix gaps without creating new ones that auditors will flag later. Reach out to us today!
How Fraxtional Makes Audit Trails Defensible

Audit trails often break down when ownership is unclear, decisions aren't properly documented, or evidence cannot withstand scrutiny. At Fraxtional, we approach audit trails not just as a technical issue but as a leadership responsibility.
Our experts help transform audit data into actionable, defensible governance.
- Clarifying Ownership: We help establish clear ownership over audit-relevant decisions, ensuring alignment across products, vendors, and jurisdictions. This guarantees accountability and consistency in your audit trail.
- Maintaining Regulatory Momentum: Our experienced leaders keep your audit processes moving smoothly through internal and external audits, sponsor bank reviews, and AML/BSA monitoring.
- Strengthening Decision Accountability: We ensure critical decisions, such as overrides and risk trade-offs, are clearly documented and tied to the right authority, making your audit trail a reliable source of evidence.
- Translating Data for Leadership: We simplify complex audit trail data into concise risk summaries for your leadership team. This clarity reduces audit friction and prevents the "explain it later" risks that often arise under scrutiny.
- Building Scalable Audit Trail Systems: We ensure audit trails become a repeatable assurance layer that grows with your business. We provide senior leadership oversight without locking you into costly, full-time hires, creating long-term value.
Through a leadership-driven model, audit trails stop being a compliance checkbox and become an essential tool for governance, risk management, and strategic growth.
Partner with Fraxtional to build audit trails that hold up when regulators, banks, and investors look deeper.
Conclusion
Modern platforms make it easy to record activity, but they don't guarantee that actions can be reconstructed, explained, or defended months or years later. Regulators, sponsor banks, and investors still look for clear accountability - not just timestamps and logs.
That's why the future of audit readiness isn't purely technical or purely procedural. It sits at the intersection of automation and leadership. Systems capture what happened. Leadership makes it credible.
For FinTech and regulated teams that understand this, audit trails become more than a compliance requirement. They become a trust mechanism that shortens audits, reduces follow-ups, and supports growth under increasing scrutiny.
Fraxtional helps teams build audit trails that go beyond mere existence by pairing strong systems with accountable oversight, turning recorded activity into defensible compliance. Reach out to us today!
FAQs
No. Audit trails are required for systems that support regulated activities or key controls. Regulators focus on systems tied to transactions, approvals, customer data, AML/BSA monitoring, and reporting - not internal tools with no compliance impact.
More detail isn’t always better. Regulators expect enough detail to reconstruct decisions end-to-end, including who acted, who approved, and why, without relying on verbal explanations.
Not necessarily. Many vendors provide logs, but logs alone don’t equal audit trails. Companies are still responsible for ensuring retention, attribution, integrity, and retrievability meet regulatory expectations.
Yes. Weak audit trails can undermine otherwise strong controls because regulators can't verify execution. In practice, this often leads to expanded exams, repeat findings, or remediation requirements.
Much earlier than most do. Audit trails become painful to retrofit after growth, vendor sprawl, or licensing. Teams that design them early avoid audit delays and sponsor bank friction later.
blogs
Don’t miss these
Let’s Get Started
Ready to Strengthen Your Compliance Program?
Take the next step towards expert compliance solutions. Connect with us today.




